Today I am going to publicly disclose a critical vulnerability I have found during my research in PayPal, This vulnerability enabled me to completely bypass the CSRF Prevention System implemented by PayPal, The vulnerability is patched very fast and PayPal paid me the maximum bounty they give ;).
1- Reusable CSRF Token:
The CSRF token “that authenticate every single request made by the user” which can be also found in the request body of every request with the parameter name “Auth” get changed with every request made by user for security measures, but after a deep investigation I found out that the CSRF Auth is Reusable for that specific user email address or username, this means If an attacker found any of these CSRF Tokens, He can then make actions in the behalf of any logged in user.
Hmm, it seems interesting but still not exploitable, as there is no way for an attacker to get the “Auth” value from a victim session.
2- Bypassing the CSRF Auth System:
The CSRF Auth verifies every single request of that user, So what If an attacker “not logged in” tries to make a “send money” request then PayPal will ask the attacker to provide his email and password, The attacker will provide the “Victim Email” and ANY password, Then he will capture the request, The request will contain a Valid CSRF Auth token Which is Reusable and Can authorise this specific user requests. Upon Further Investigation, We have found out that an Attacker can obtain the CSRF Auth which can be valid for ALL users, by intercepting the POST request from a page that provide an Auth Token before the Logging-in process, check this page for the magical CSRF Auth “https://www.paypal.com/eg/cgi-bin/webscr?cmd=_send-money”. At this point the attacker Can CSRF “almost” any request on behalf of this user.
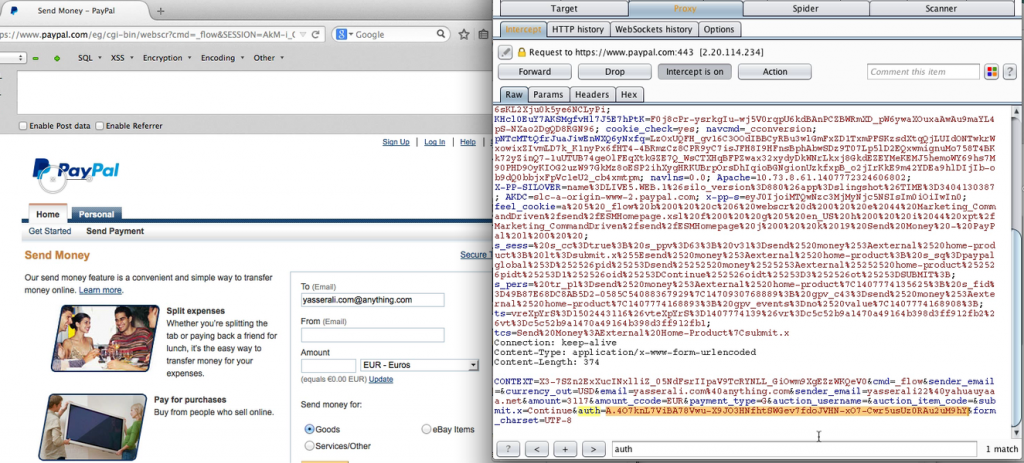
Through examination of the password change process, I have found that an attacker can NOT Change the victim password without answering the Security Questions set by user, Also the user himself can NOT change the security questions without entering the password!
3- ByPassing the Security Questions Change:
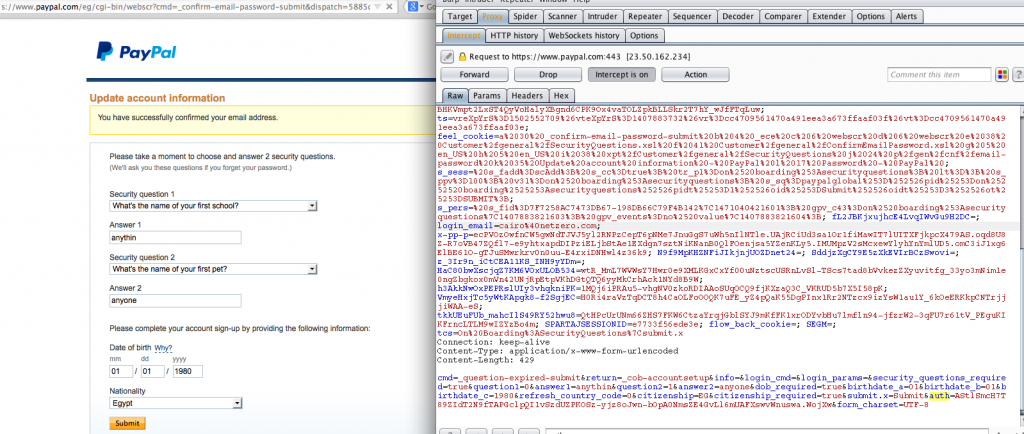
After further investigation, I have noticed that the request of setting up the security questions “which is initiated by the user while signing up” is not password-protected, and it can be reused to reset the security questions up without providing the password, hence, Armed with the CSRF Auth, an attacker can CSRF this process too and change the victim’s Security questions.
At this point, An attacker can conduct a targeted CSRF attack against PayPal users and take a full control over their accounts. Hence, An attacker can CSRF all the requests including but not limited to:
1- Add/Remove/Confirm Email address
2-Add fully privileged users to business account
3- Change Security questions
4- Change Billing/Shipping Address
5- Change Payment methods
6- Change user settings(Notifications/Mobile settings) ………… and more.
To automate the whole process, I have coded a Python interactive server to demonstrate how an attacker can exploit this vulnerability in a real-life scenario attack.
Here is the POC Video:
Update #1 (Dec 4th 2014):
PayPal spokesperson released the following statement:
“One of our security researchers recently made us aware of a potential way to bypass PayPal’s Cross-Site Request Forgery (CSRF) Protection Authorization System when logging onto PayPal.com. Through the PayPal Bug Bounty program, the researcher reported this to us first and our team worked quickly to fix this potential vulnerability before any of our customers were affected by this issue. We proactively work with security researchers to learn about and stay ahead of potential threats because the security of our customers’ accounts is our top concern.”
Update #2 (Dec 31st 2014)”
Made the 3rd Rank in Top Ethical Hackers of 2014 , CheckMarx Company
Update #3 (March 20th 2015):
This technique has been listed on the ( TOP 10 Web Hacking techniques of 2014) with the rank #6.
Pingback: Hacking PayPal Account with a single exploit | Security Affairs
How much did you get? Saying you got the max and then not saying how much is it sounds a bit unfair 🙂
Yeah tell us !
10,000 USD 🙂
MSA , congrats bro i hope you the best ISA
Pingback: PayPal patches vulnerability that could have let an attacker hijack anyone’s account (updated) - Reader
Pingback: Yasser Ali’s Blog » Hacking PayPal Accounts with one click | whitehatnews.com
Hi Yasser,
I don’t really understand the part about visiting yasserali.com:8080/w3pwn
What information is being captured in that XXS request? Was that necessary just for adding another email address, or password reset or both? Can I say that if the user didn’t click on the link, this attack is rather difficult to reproduce?
Brendan
CSRF attack needs a user interaction, in this attack the victim has to click on the link, that’s it, regarding the Auth-Token, the attacker could get a valid Auth-Token from any request happens when the in an anonymous session.
Thanks for the explanation. Can I access the python script code?
Is the auth in the HTTP_REFERER?
How much was the bounty? That’s what we really want to know 🙂
10,000.00 USD 🙂
Hi Yasser Ali, Can you make a better video, IE Zoom on those commands ETC? Or even Speech? Thanks for you’re time, And lovely hack.
Yasser Ali, I cant see what you are typing ETC.
Set the video quality to 1080px
Hi Yaseer,
Any possibility of sharing the python code ? 😛
Nice one, congrats 🙂
Holy hell you must be one happy camper with $10k USD.
Tell us about yourself, what do you do? Age?
I am 28, I do security consultation 🙂
Actually they paid the mudslime in falafel vouchers 🙂 Bug ruining douche.
Hi, I am very impressed by your achievement. It would be nice if you can share me how you learnt your skill in Information Security. I mean which books or websites?
When did you report this and how many days did they take to fix it?
I honestly think you deserve more. Some services offer up to 1 million for those who discover vulnerabilities in their security. This vulnerability wasn’t a Gmail, iCloud or SnapChat one, it was on an online banking/money transfer site. The consequences could have been huge and purely financial to the company.
Really this was a nice catch… Congrats Yasser bro (y) 😀
Pingback: PayPal patches vulnerability that could have let an attacker hijack anyone’s account (updated) | SomeLearning
That was nice!! How long did it take for you to do all this ?
I got the idea while walking in the street, Then It takes some hours to bypass the security questions and write the Python Script.
So there were two main issues:
1. You was be able to get universal (for all users) CSRF-token from _send-money form
2. There were no password protection for adding mail and changing questions
Is it correct?
yes, but there was a password protection on the “changing questions”, but I have bypassed this by calling the “set”questions function instead of calling the “Reset” questions function and successfully overwrote the already set questions ;), clear now?
Yes, thanks! Good job:)
السلام عليكم,
كيفك علي؟
كاتبين مقالة عن مدونتك على موقع سوفتبيديا, رابط المقالة:
http://news.softpedia.com/news/Critical-PayPal-Bug-Left-All-Accounts-Vulnerable-to-Hijacking-466500.shtml
May I copied your clip and add some explanation in Thai? I will link back to original clip.
Go ahead, share knowledge 🙂
Hi Yaser,
Excelennet ctach
What baffles me however that connection with paypal site is not SSL protected!!!!
If it was your hack would be impossible to realise… Or i am missing something?
It is SSL protected bro!
Hi Yasser,
I’ve been to fast to post my previous comment, but now i’m baffled even more!!!
Paypal DO use SSL…. So i’m at loss how you managing to get the plaintext of the session?
I am intercepting my own traffic using burpsuite, Where is the problem?
Pingback: Hacking PayPal Accounts With CSRF | Hackaday
Pingback: Hacking PayPal Accounts With CSRF - Tech key | Techzone | Tech data
I have detected one such CSRF payload that has the potential to CSRF all Paypal functions. Paypal is presently working on that issue. Not sure how much they are going to pay me for that.Could you please tell how many days did they take to fix that issue for yours? What categorization had they assigned to that issue? For me they categorized that as CSRF though, it is not a normal CSRF.
Hi Yasser,
did you get a chance to look at my comment?
Amlan
yes I have talked to you on Facebook and you didn’t respond, DM on twitter
I guess, you have contacted wrong Amlan. My twitter ID @whitesec1211 🙂
Thanks
Sorry Yasser,
I’m not really pentest expert… but browsing thru burpsuite docs i’m trying to understand how it works in you case. I suppose that you’ve installed burp CA certificate into the trust chain of your browser, and thew burp proxy tool generated for you a certificate for http://www.paypal.com for it’s MITM functionality… Am i right? If so it seems to me that an attacker who is trying to intercept traffic from another’s person browser will have much bigger challenge before him as he will have to BREAK the SSL encryption without the help
of cooperating browser. Or i am missing something else?
P.S. I’m not trying to criticise your achievement, it is pretty brilliant work IMO
Vadim, it’s not a man in the middle attack but a CSRF attack. If you’re not familiar with CSRF you can look up the wikipedia article, it explains the basics pretty well. The TL;DR is that you trick the user into sending the right http request to paypal’s website by e.g. making them click a link or load an “image”.
Hi Michal,
Thanks you for the pointer, i’we brought myself up to date about CSRF attacks, so to summarize:
I attempt an unsuccesful login to paypal using victims’s credentials,
while using burp to decode the traffic and recover auth token.
Than i trick user to send an https request (email/password change for example) to the paypal with the auth
token i collected?
Michal made it clear, A hacker doesn’t need to be MITM, Go to OWASP and read about the CSRF attack
Pingback: Investigador demuestra el hackeo a PayPal
Hi Yasser,
Few clarifications about this issue. Is it like
1. You navigated to the page https://www.paypal.com/eg/cgi-bin/webscr?cmd=_send-money
2. try to transfer money
3. Paypal asks for credential
4. Let’s say, you provided [email protected](victim email) and a wrong password (as you dont know victim’s password)
5. You captured the auth token in Burp Suite and forwarded the authentication request(which ofcourse will fail as the password was wrong) But the auth token used in this request can now be reused for victim id [email protected]
6. You created a CSRF payload with the captured auth token and sent that to [email protected] as a targeted attack
7. If the user bearing paypal id [email protected], when logged into Paypal, clicks on the link sent by you, fall victim to your trap.
Am I correct?
Best
Amlan
Yes right, but you don’t have to enter or know the victim email to capture the Auth Token, you can just enter any random value, No need for victim email.
Pingback: Hacking PayPal Accounts With CSRF | Hack The Planet
Pingback: PayPal Accounts Takeover Vulnerbility | TAR News
Pingback: ste williams – All PayPal accounts were 1 click away from hijacking
A think that I didn’t understand from your clip is about the python script.
As my understanding, when victim visit a trap, then the vimtim is a person to send information, am I right? so, the script is just like a tunnel to let attracker pass needed information to let victim browser send a request to Paypal as what attacker want.
So, request send to Paypal doesn’t use the difference session, the attacker use vimtim session with given token pass though the tunnel. right? are you be able to provide script to get more understanding?
PS. I have put your content here https://www.youtube.com/watch?v=kmPqMUkFkHg
The attacker can generate a CSRF which is valid for everybody, The python script is just for automating the process and making the exploit powerful, I have seen your video, Amazing 😉
Pingback: Hacking PayPal Account with Just a Click « About Hacker
Pingback: Hackear cuenta PayPal con sólo un clic - F403MX
Pingback: Sony Breach & More – WSWiR Episode 131 - Varanoid.com
Pingback: Sony Breach & More – WSWiR Episode 131
Pingback: Hacking PayPal Account with Just a Click | handleweb.net
Pingback: PayPal hackable in one click according to security researcher | ITProPortal.com
Pingback: Researcher Shows How To Hack Any PayPal Account In Just One Click. | Hack Read
I do believe that I have been hacked. Pay Pal and E-bay have both denied this but I have a zero bank balance. Right here at Christmas. No one can seem to help me especially not the “big” conglomerates that ignore the problems and “deny,deny,deny. I will proceed with whatever means that ae available to me. Now that I have been robbed by these “hackers” and no money left for presents , its a sad sad thing. Huum I have no choice bu tto move forward …thanks for letting me vent.
To you all.. Have a great Christmas!
(oh btw) first time I had ever ordered on e-bay.
I think you have been a victim of a scam not hacking, you should never give-up, follow up with your issue until you get all your rights back.
Pingback: Il était possible de pirater Paypal d’un clic de souris | Data Security Breach
Pingback: 150 Million PayPal Accounts In Danger of Hijacking - Patriot Rising
Pingback: В системе защиты от подделки запросов PayPal обнаружена серьезная уязвимость | Zit@i0
the hijacked money actually is mine.can u plz resend me back.
ha ha waiting for approval ../ good. can i get your Facebook id?
Contact me on twitter and I will DM you my Facebook
ok I will 😀
Pingback: В системе защиты от подделки запросов PayPal обнаружена серьезная уязвимость | Malanris's site
Pingback: PayPal vulnerable a CSRF (solucionado) - SABIAS UN DATO
Pingback: Security Predictions for 2015 - InfoSec Institute
Dear Yasser,
May I please have the source to your python program to help me learn more about information security, i know that it doesn’t work but I just want to look at the source
Pingback: Security Predictions for 2015 | OSINFO
Pingback: Top 10 Web Hacking Techniques of 2014 | WhiteHat Security Blog
Pingback: Sony Breach & More – WSWiR Episode 131 | Everything You Need to Take Threats Head On
Pingback: Information Security Breach Report – 04 December 2014 | SRM Blog
Hi Yasser…i am a newbie also and i want to learn…can you provide the source code please??…want to research …
The source code has nothing to do with research!
what tools did you use? sorry noobie, still learning
Just burp proxy 🙂
Pingback: Kritična ranjivost u PayPalu | My Blog
Pingback: В системе защиты от подделки запросов PayPal обнаружена серьезная уязвимость | FNIT.RU
Pingback: Top 10 Web Hacking Techniques of 2014 | ASZone
Is the vuln still active? A lot of hackings regarding paypal this month.
كيف يا هندسه
can i add money to my paypal
Nope, PayPal is secure
Brilliant, loved it 😀
I think you entered an invalid Email ( in text input >>from email) ……[email protected]
But to Whom this Token as it isn`t a valid Email !!!!!?
This was a Valid-For-All token, a token which not associated with any session, so it will be valid for any session!
hey bro dont hack mine i aslo connected wid us pls
nice
hi video link please give
I have uploaded a new video, kindly refresh the page
Pingback: Hacking of Paypal Acoount By Just a Click By Yasser Ali – Simentify
nice work bro…congratsss 🙂
GreaT 😀
#RESPECT
I’m Trying Since 3month Nothing HAPPENED 🙂
Pingback: Web Application Security & Bug Bounty (Methodology, Reconnaissance, Vulnerabilities, Reporting) – Welcome Hackers!
Pingback: Web Application Security & Bug Bounty – CodeCraver
Pingback: Guide 001 |Getting Started in Bug Bounty Hunting.. – Muhammad Khizer Javed
Pingback: Bug Bounty Methodology (TTP- Tactics,Techniques and Procedures) V 2.0 ~ Cyberzombie
Pingback: Getting Started in Bug Bounty Hunting | Complete Guide